Top Website Security Best Practices for 2025
This article was assisted with AI. We may include links to partners.
Your website is a primary business tool, not just a digital storefront. It's how customers find you, trust you, and transact with you. However, with this visibility comes significant risk. Many small business owners and freelancers mistakenly believe their sites are too small to attract cyber threats, but automated bots and malicious actors constantly scan the internet for vulnerabilities, making every website a potential target. A security breach can lead to data loss, reputational damage, and significant financial costs.
This guide cuts through the technical jargon to provide a clear, actionable list of website security best practices for non-technical users. You will learn how to implement crucial defenses, from basic SSL/TLS encryption to advanced security headers, without needing a degree in cybersecurity. To fully grasp the threats your website faces, it is essential to implement robust cyber security risk management strategies. This article offers a practical roadmap to fortify your digital presence, ensuring your business data, customer information, and reputation remain secure. Let’s dive into the concrete steps you can take today.
1. HTTPS and SSL/TLS Implementation
Securing the connection between your website and its visitors is the first line of defense. This is done with HTTPS (Hypertext Transfer Protocol Secure), which uses an SSL/TLS certificate to encrypt all data exchanged, like passwords or credit card numbers. Think of it as a secure, sealed envelope for information traveling between your site and a visitor's browser. Without it, that information is like a postcard that anyone can read.
Implementing HTTPS is non-negotiable. Modern browsers like Google Chrome mark all non-HTTPS sites as "Not Secure," which can scare away visitors. Search engines also favor secure sites, giving you a slight SEO advantage.
Actionable Steps for Implementation
- Get an SSL/TLS Certificate: Ask your hosting provider for a free certificate from Let's Encrypt. Most hosts offer a one-click installation for this.
- Force HTTPS on All Pages: After installing the certificate, set up your server to automatically redirect all traffic from
http://tohttps://. This ensures every visitor uses the secure connection. Your hosting provider's support can help with this. - Strengthen Your Configuration: For advanced security, ask your developer or host to add an HSTS (HTTP Strict Transport Security) header. This tells browsers to only communicate with your site over HTTPS, preventing certain types of attacks.
The following infographic highlights a few key statistics that underscore the importance and feasibility of implementing HTTPS.
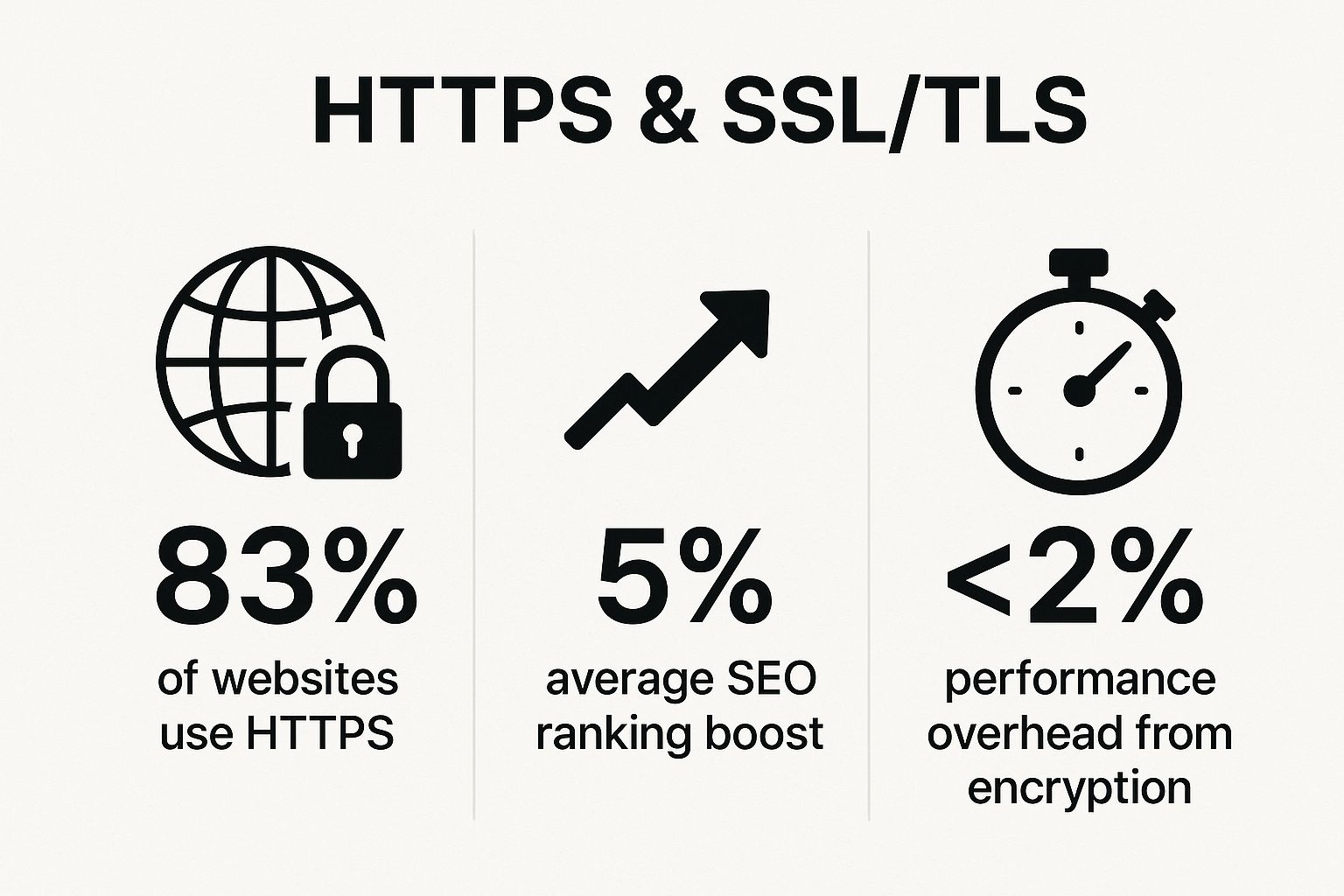
These numbers clearly show that HTTPS is not only the industry standard but also a beneficial practice with minimal performance impact.
2. Strong Authentication and Multi-Factor Authentication (MFA)
A strong password isn't enough to protect important accounts. Multi-factor authentication (MFA) adds a crucial second layer of security. It requires users to provide two or more forms of proof to log in: something they know (password), something they have (a code from their phone), or something they are (a fingerprint). This means that even if a criminal steals your password, they still can't get into your account.
Implementing MFA is a fundamental security practice. It transforms a single, vulnerable password into a robust, multi-layered checkpoint, making it much harder for attackers to break in.

Actionable Steps for Implementation
- Enable MFA on All Admin Accounts: Your top priority is securing accounts with administrative privileges, like your website's WordPress login or your hosting control panel.
- Choose Authenticator Apps Over SMS: When setting up MFA, use an app like Google Authenticator or Authy. Text message (SMS) codes can be intercepted through "SIM-swapping" attacks, making authenticator apps a more secure choice.
- Set Up Backup Methods: Always create backup options, like saving a set of recovery codes or adding a secondary security key. This prevents you from being permanently locked out if you lose your phone.
This video from Google provides a simple yet effective explanation of how MFA, specifically two-step verification, works to keep your accounts secure.
By making MFA a standard practice, you significantly raise the bar for attackers and protect the integrity of your website and user data.
3. Regular Security Updates and Patch Management
Outdated software is a top target for hackers because it has known security holes that are easy to exploit. Regularly updating your website's software—including its content management system (CMS), plugins, and themes—is like locking the doors and windows of your house. It closes known vulnerabilities before criminals can take advantage of them.
Neglecting updates leaves your site exposed. Attackers use automated tools to scan for websites running old software. A disciplined update process is a proactive, non-negotiable task that protects your site from the most common types of attacks.
Actionable Steps for Implementation
- Turn on Automatic Updates: For your CMS (like WordPress) and its plugins, enable the automatic update feature for security releases. This ensures critical patches are applied as soon as they are available.
- Use a Staging Site for Major Updates: Before applying a major update to your live website, test it on a staging site—a private copy of your site. This lets you check for any issues or conflicts without risking your live traffic.
- Keep an Inventory of Your Software: Make a simple list of all software, plugins, and themes your website uses. This helps you track what needs updating and respond quickly when a new vulnerability is announced.
- Subscribe to Security News: Follow security alerts for the software you use (e.g., the official WordPress security blog). This keeps you informed about emerging threats so you can act fast.
4. Input Validation and Sanitization
Never trust data submitted by users through forms, search bars, or comment sections. Attackers can insert malicious code into these fields to hijack your website or steal data. Input validation and sanitization is the process of checking and cleaning all user-submitted data before your website processes it. This is your main defense against common attacks like SQL injection and Cross-Site Scripting (XSS).
Failing to validate input is like letting a stranger bring an unchecked package into your office. By implementing strict checks, you ensure that only safe, properly formatted data enters your system, protecting your database and your users.
Actionable Steps for Implementation
- Use Server-Side Validation: Always validate data on your server, not just in the user's browser. Browser-level checks are easy for attackers to bypass. Your contact form plugin or e-commerce platform should handle this for you.
- Use Parameterized Queries for Databases: This is a technical but critical point for your developer. Instead of mixing user data directly with database commands, use parameterized queries. This method treats all user input as simple text, not executable code, which effectively blocks SQL injection attacks.
- Clean Data Before Displaying It: Before showing user-generated content (like comments or profile information) on a page, it must be "sanitized." This means converting special characters into plain text so a browser doesn't execute them as code. Most modern frameworks and CMS platforms do this automatically.
5. Content Security Policy (CSP)
A Content Security Policy (CSP) is an advanced security feature that tells a visitor's browser which sources are approved to load content (like scripts, images, and stylesheets) on your website. By creating an "allowlist" of trusted domains, you can prevent the browser from loading malicious assets injected by an attacker. This is a powerful defense against attacks like Cross-Site Scripting (XSS).
Implementing a CSP gives you precise control over your site's resources, stopping unauthorized scripts from running and stealing sensitive user data. It's a proactive security measure used by major sites like Google and GitHub to protect their users.
Actionable Steps for Implementation
- Start in Report-Only Mode: Ask your developer to first implement the CSP in "report-only" mode. In this mode, the browser will report any violations without actually blocking the content. This is a safe way to build your policy and see what you need to allowlist before enforcing it.
- Define Your Rules: Work with your developer to carefully define the sources for scripts (
script-src), styles (style-src), and other resources. A good starting point is to only allow resources from your own domain ('self'). - Use a CSP Evaluation Tool: Use free online tools like Google's CSP Evaluator to check your policy for common mistakes or overly permissive rules. This helps ensure your CSP is effective.
6. Secure Session Management
A "session" is what allows a user to stay logged in as they navigate your website. It's identified by a unique session ID stored in the browser. Secure session management ensures these IDs are created and handled safely, preventing attackers from stealing a user's session and taking over their account.
If session IDs are not protected, an attacker can hijack a valid session and impersonate a legitimate user. This can lead to a serious data breach. Protecting sessions is one of the most vital website security best practices for any site with user accounts.
Actionable Steps for Implementation
- Transmit Session IDs Securely: Ensure your entire website uses HTTPS. This encrypts the session ID as it travels between the user's browser and your server, making it difficult to steal.
- Create a New Session ID on Login: When a user logs in, your website should generate a brand-new session ID. This prevents "session fixation" attacks, where an attacker tricks a user into using a session ID that the attacker already knows.
- Set Short Session Timeouts: Automatically log users out after a reasonable period of inactivity (e.g., 15-30 minutes). This shortens the window of opportunity for an attacker to use a stolen or abandoned session.
- Store Sensitive Data on the Server: Avoid storing sensitive information like user permissions directly in the browser's session cookie. Store that data on your server and use the session ID simply to look it up.
7. Database Security and SQL Injection Prevention
Your website's database holds its most valuable assets, including customer data, orders, and user credentials. Protecting it is non-negotiable. Database security involves multiple layers of defense, including strict access controls, data encryption, and strong protection against attacks like SQL injection.
SQL injection happens when an attacker inserts malicious database commands into a web form, like a search bar or login field. If successful, they can view, change, or delete your data. Implementing strong database security is a core practice for safeguarding your business's most critical information.
Actionable Steps for Implementation
- Use Parameterized Queries: This is the most effective way to stop SQL injection. It's a coding practice that separates user input from database commands, treating all input as simple data, not executable code. Your developer must implement this.
- Apply the Principle of Least Privilege: Your website should connect to the database using an account with the minimum permissions needed. For example, an account that only needs to read product information should not have permission to delete customer data. This limits the damage if the account is compromised.
- Encrypt Sensitive Data: Work with your developer or hosting provider to encrypt sensitive data stored in your database, such as personal user information. This ensures that even if an attacker gains access to the database files, the data remains unreadable.
8. Web Application Firewall (WAF) Implementation
A Web Application Firewall (WAF) is a protective shield that sits between your website and the internet. It inspects incoming traffic and blocks common attacks like SQL injection and cross-site scripting (XSS) before they can reach your server. Think of it as a security guard for your website.
A WAF is a powerful and proactive security tool. Cloud-based services like Cloudflare or Sucuri make WAFs accessible and easy to set up for any business, providing an essential layer of defense that can block threats automatically.

Actionable Steps for Implementation
- Choose a WAF Service: Cloud-based WAFs like Cloudflare (which has a free plan) are great for non-technical users because they are easy to activate. Many hosting providers also offer a WAF as an add-on service.
- Enable the Core Rule Set: Once activated, enable the default or core rule set provided by the WAF service (e.g., the OWASP Core Rule Set). This immediately protects your site against a wide range of common attacks.
- Monitor for False Positives: When you first enable a WAF, occasionally check its logs to ensure it isn't blocking legitimate visitors. Most modern WAFs are well-tuned, but it's good practice to review the activity to ensure everything is working correctly.
- Use WAF Logs to Understand Threats: The logs from your WAF can show you what kinds of attacks are targeting your site. This information is valuable for understanding your risks and strengthening your overall security.
9. Security Headers Implementation
HTTP security headers are instructions your server sends to a visitor's browser, telling it how to behave securely. These headers can prevent common attacks like cross-site scripting (XSS) and clickjacking (where an attacker tricks a user into clicking something disguised). They act as a set of security rules that harden your website at the browser level.
Implementing security headers is a simple but highly effective practice. It adds another layer of defense that works automatically to protect your users, making it a key part of modern website security best practices.
Actionable Steps for Implementation
- Scan Your Website's Headers: Use a free tool like securityheaders.com to check your site's current security headers. The tool will give you a grade and tell you which headers are missing.
- Add Key Security Headers: Ask your developer or hosting provider to add the recommended headers to your server configuration. The most important ones are:
Strict-Transport-Security(HSTS),X-Frame-Options,X-Content-Type-Options, andContent-Security-Policy(CSP). - Test After Implementing: After adding the headers, browse your website to make sure everything still works correctly. A misconfigured header, especially CSP, can sometimes break parts of your site, so it's important to test.
9-Point Website Security Practices Comparison
| Security Measure | Implementation Complexity | Resource Requirements | Expected Outcomes | Ideal Use Cases | Key Advantages |
|---|---|---|---|---|---|
| HTTPS and SSL/TLS Implementation | Low (often 1-click install) | Low (free certificates available) | Encrypted data, user trust, SEO boost | All websites | Prevents data snooping, a modern web standard |
| Strong Authentication and MFA | Low (enable in account settings) | Low (free authenticator apps) | Drastically reduced account takeover risk | All admin and user accounts | Protects against stolen passwords |
| Regular Security Updates and Patch Management | Low (use auto-updates) | Low (requires consistent checks) | Closes known security holes | All software, CMS, and plugins | Prevents attacks on known vulnerabilities |
| Input Validation and Sanitization | High (requires careful coding) | Moderate (developer time) | Prevention of injection and XSS attacks | Sites with forms or user content | Stops database attacks and malicious scripts |
| Content Security Policy (CSP) | High (requires testing and tuning) | Low (server configuration) | Prevents XSS, controls resource loading | Complex sites with many scripts | Granular control over site assets |
| Secure Session Management | Moderate (server-side configuration) | Moderate (developer time) | Prevents session hijacking | Sites with user logins | Protects logged-in user accounts |
| Database Security and SQL Injection Prevention | High (secure coding and configuration) | Moderate (developer and DB admin time) | Prevents data theft and manipulation | Data-driven applications | Protects your most valuable data |
| Web Application Firewall (WAF) | Low (cloud service activation) | Low to Moderate (free to paid plans) | Blocks common attacks automatically | All public-facing websites | Immediate protection without code changes |
| Security Headers Implementation | Low to Moderate (server configuration) | Low (a few lines of code) | Protects against browser-level attacks | All websites | Easy, high-impact security boost |
Your Next Step: Making Security a Standard, Not an Afterthought
Navigating website security can feel overwhelming, but implementing website security best practices is a fundamental requirement for building a trustworthy online presence. The goal is to view security not as a one-time task, but as an ongoing part of your digital strategy.
The path to a secure website is built on layers of proactive defense. We’ve covered critical steps, from encrypting data with SSL and implementing security headers to deploying a Web Application Firewall (WAF) to block malicious traffic. We also touched on code-level diligence, like validating user input to prevent XSS and using parameterized queries to stop SQL injection. Each practice is another crucial barrier against threats.
From Theory to Action: Your Immediate Priorities
Your immediate action plan should focus on a few core principles. First, master the fundamentals. This means using strong, unique passwords for all accounts and enabling Multi-Factor Authentication (MFA) everywhere you can. This one step dramatically raises the difficulty for attackers.
Second, commit to consistency. Security is not "set it and forget it." Regularly updating your CMS, plugins, and themes is your best defense against newly discovered vulnerabilities. Make this a recurring, non-negotiable task.
Finally, leverage smart tools. You don't have to be a security expert. Modern platforms are designed to handle much of the heavy lifting. A quality hosting provider often includes WAF services, and many website platforms have built-in features for adding security headers or a Content Security Policy (CSP).
The Real Impact of a Secure Digital Foundation
Ultimately, the value of these website security best practices goes far beyond preventing a breach. A secure website is a sign of professionalism and reliability. It shows customers you value their privacy and are a trustworthy partner. This trust leads to greater customer loyalty, higher conversion rates, and a stronger brand reputation. By proactively building a secure digital foundation, you’re not just protecting data; you’re safeguarding your business’s future.
Ready to build a powerful website without getting bogged down in complex security configurations? The Solo AI Website Creator handles the essentials for you, automatically implementing SSL certificates and building on a secure foundation so you can focus on growing your business with confidence. Create your secure, professional website in minutes at Solo AI Website Creator.
